25+ network architecture diagram in computer networks
Was founded in Palo Alto California in October 2003 by Andy Rubin Rich Miner Nick Sears and Chris White. In the OSI reference model the communications between a computing system are split into seven different abstraction layers.
What Is Network Architecture What Do Network Architects Really Do How Can I Become A Network Architect Quora
Early networks before the introduction of X25 and the OSI model.

. Large clouds often have functions distributed over multiple locations each location being a data centerCloud computing relies on sharing of resources to achieve coherence and typically. This gallery contains network diagrams for wireless wired and hybrid home networks. The main function of this is to carry the data in the bits form through the Local Area Network LAN.
This type provides access to an enterprise network such as an intranetThis may be employed for remote workers who need access to private resources or to enable a mobile worker to access. A network router is one kind of network device in a computer network and it is used for routing traffic from one network to another. Rubin described the Android project as having tremendous potential in developing smarter mobile devices that are more aware of its owners location and preferences.
It characterizes networked structures in terms of nodes individual actors people or things within the network and the ties edges or links relationships or interactions that connect them. Physical Data Link Network Transport. Research into packet switching at the National.
AWS applications and services are available all over the world 24 hours a day and systems may be readily deployed to. Network diagrams are often drawn with professional drawing software tools. Architecture ZTA uses zero trust principles to plan industrial and enterprise infrastructure and.
A computer system is a complete computer that includes the. Cloud computing is the on-demand availability of computer system resources especially data storage cloud storage and computing power without direct active management by the user. Since 2017 there have existed supercomputers which can perform over 10 17 FLOPS a hundred quadrillion FLOPS.
Computer security cybersecurity cyber security or information technology security IT security is the protection of computer systems and networks from information disclosure theft of or damage to their hardware software or electronic data as well as from the disruption or misdirection of the services they provide. A computer is a digital electronic machine that can be programmed to carry out sequences of arithmetic or logical operations computation automaticallyModern computers can perform generic sets of operations known as programsThese programs enable computers to perform a wide range of tasks. For instance in a copper cable network the bits in the form of electrical signals whereas in a fiber network the bits are available in the form of light.
A supercomputer is a computer with a high level of performance as compared to a general-purpose computerThe performance of a supercomputer is commonly measured in floating-point operations per second instead of million instructions per second MIPS. These interconnections are made up of telecommunication network technologies based on physically wired optical and wireless radio-frequency. Get 247 customer support help when you place a homework help service order with us.
In data communication it works like a physical path between the sender the receiver. YOLOv5 adopts Path Aggregation Network PANet structure as its neck based on Feature Pyramid Networks FPN structure which enhances bottom-up path and improves propagation of underlying. The connections of the biological neuron are.
The Amazon Web Service architecture enables users to receive the finest possible service regarding web services innovations such as introducing or deleting virtual servers service choices and so on. Michael Heine is a CompTIA-certified writer editor and Network Engineer with 25 years experience working in the television defense ISP telecommunications and education industries. The X25 era when many postal telephone and telegraph PTT companies provided public data networks with X25 interfaces.
A computer network is a set of computers sharing resources located on or provided by network nodesThe computers use common communication protocols over digital interconnections to communicate with each other. It also covers sensors and other devices such as programmable logic controllers which interface with process plant or machinery. Jaringan yang saling berhubungan adalah sistem jaringan komputer yang saling terhubung secara global dengan menggunakan paket protokol internet TCPIP untuk menghubungkan perangkat di seluruh duniaIni adalah jaringan dari jaringan yang terdiri dari jaringan privat publik akademik bisnis.
Supervisory control and data acquisition SCADA is a control system architecture comprising computers networked data communications and graphical user interfaces for high-level supervision of machines and processes. On the ARPANET the starting point for host-to-host communication in 1969 was the 1822 protocol which defined the. There are different types of network diagrams provided by EdrawMax and you can get started with it now.
The field has become of significance due to the. And the Internet era. Thus a neural network is either a biological neural network made up of biological neurons or an artificial neural network used for solving artificial intelligence AI problems.
Zero trust assumes there is no implicit trust granted to assets or user accounts based solely on their physical or network location ie local area networks versus the internet or based on asset ownership enterprise or personally owned. Remote access A host-to-network configuration is analogous to connecting a computer to a local area network. Internet lakuran bahasa Inggris dari interconnected network.
Efforts to search for slimmer architecture and sparse networks given a full model demonstrated that sparse models can decrease storage requirements and improve computational performance 161718. The Open Systems Interconnection model OSI model is a conceptual model that provides a common basis for the coordination of ISO standard development from the purpose of system interconnection. Virtual private networks may be classified into several categories.
We will guide you on how to place your essay help proofreading and editing your draft fixing the grammar spelling or formatting of your paper easily and cheaply. Each network diagram includes a description of the pros and cons of. Social network analysis SNA is the process of investigating social structures through the use of networks and graph theory.
For example here a router is considered as traffic police at the junction he directs dissimilar traffic networks to dissimilar directions. One of the first uses of the term protocol in a data-commutation context occurs in a memorandum entitled A Protocol for Use in the NPL Data Communications Network written by Roger Scantlebury and Keith Bartlett in April 1967. The network diagram is a schematic depicting the nodes and connections amongst nodes in a computer network or more generally any telecommunications network.
Leonhard Euler ˈ ɔɪ l ər OY-lər German. A neural network is a network or circuit of biological neurons or in a modern sense an artificial neural network composed of artificial neurons or nodes. The early intentions of the company were to develop an advanced operating.
ACM Transactions on Recommender Systems TORS will publish high quality papers that address various aspects of recommender systems research from algorithms to the user experience to questions of the impact and value of such systemsThe journal takes a holistic view on the field and calls for contributions from different subfields of computer science and. Examples of social structures commonly visualized through. The history of packet-switched networks can be divided into three overlapping eras.
15 April 1707 18 September 1783 was a Swiss mathematician physicist astronomer geographer logician and engineer who founded the studies of graph theory and topology and made pioneering and influential discoveries in many other branches of mathematics such as analytic number theory complex analysis and infinitesimal. These two networks could be private to a public company network.

Introduction To Graph Theory And Its Implementation In Python Graphing Data Visualization Types Of Graphs

What Is Zero Trust Vmware Security Blog Vmware
How Many Different Types Of Computer Networking Are There Quora
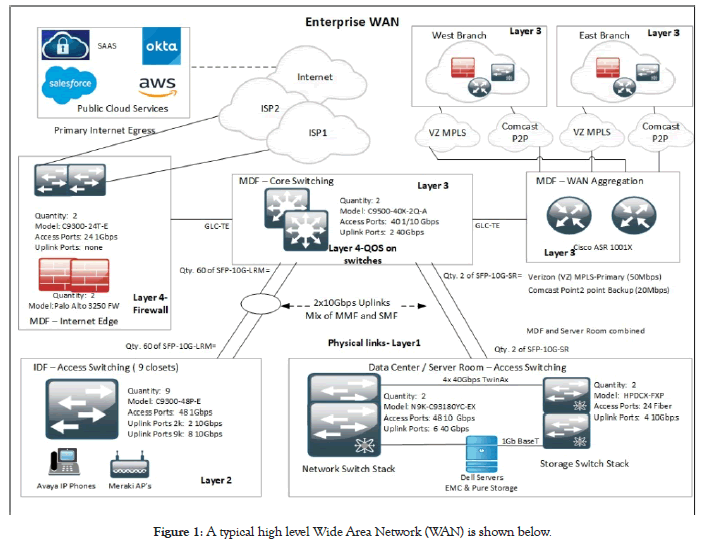
Enterprise Network Hardware Refresh

Antakya Biennial Artists Network 2010 Burak Arikan 3b Art21 Magazine Artist Creative Art Art Google
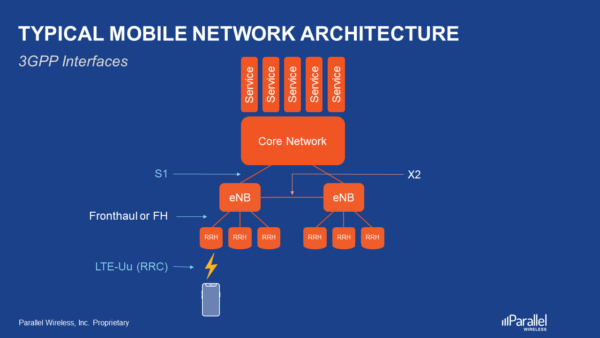
Why We Need The Open Ran Movement Even Though 3gpp Interfaces Are Already Open Parallel Wireless

Broadcast Wiring Sometimes Simple Is Beautiful Structured Cabling Home Electrical Wiring Cable Management

Network Slicing For 5g 4g 3g 2g Wi Fi Networks Parallel Wireless

Top 25 Microservices Interview Questions And Answers

Activity Network Diagram And Definition Example Study Com

What Is Zero Trust Vmware Security Blog Vmware

Network Technology Different Types Advantages And Disadvantages

How To Deploying A Ubiquiti Unifi Home Network Including Multiple Wifi Access Points Part 1 Updated Free Time

What Is Zero Trust Vmware Security Blog Vmware
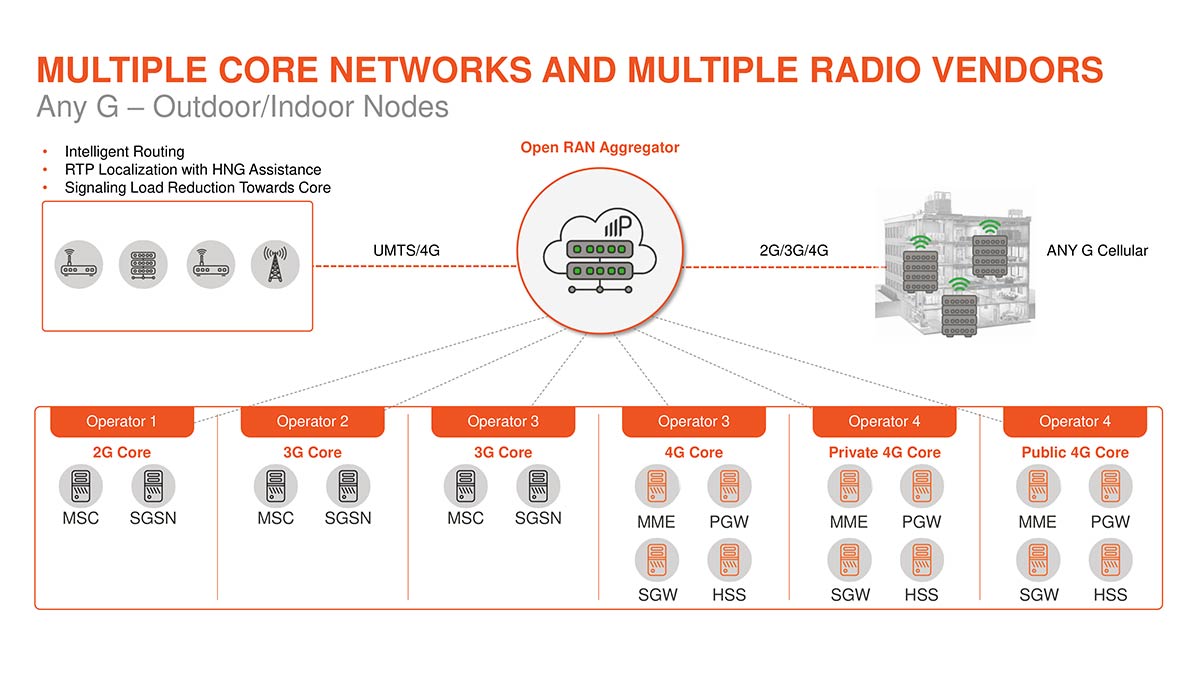
Multi Operator Core Networks Mocn Parallel Wireless

Activity Network Diagram And Definition Example Study Com

In This Blog We Will Show How Spark Sql S Apis Can Be Leveraged To Consume And Transform Complex Data Streams From Apache Kafk Apache Spark Apache Kafka Spark